Hide Global Protect VPN client as default sign-in option
With a client I am working on their modern workplace. Well.. it's not that modern, because they still want all the traffic to go to the Internet through their network. And that goes through the Palo Alto Global Protect VPN client. The customer is 👑, we say, right?
There is no clear agreement yet whether or not a VPN client should be installed, but until then, we need a VPN client. So the package is created, uploaded to Intune and is installed during the Autopilot process.
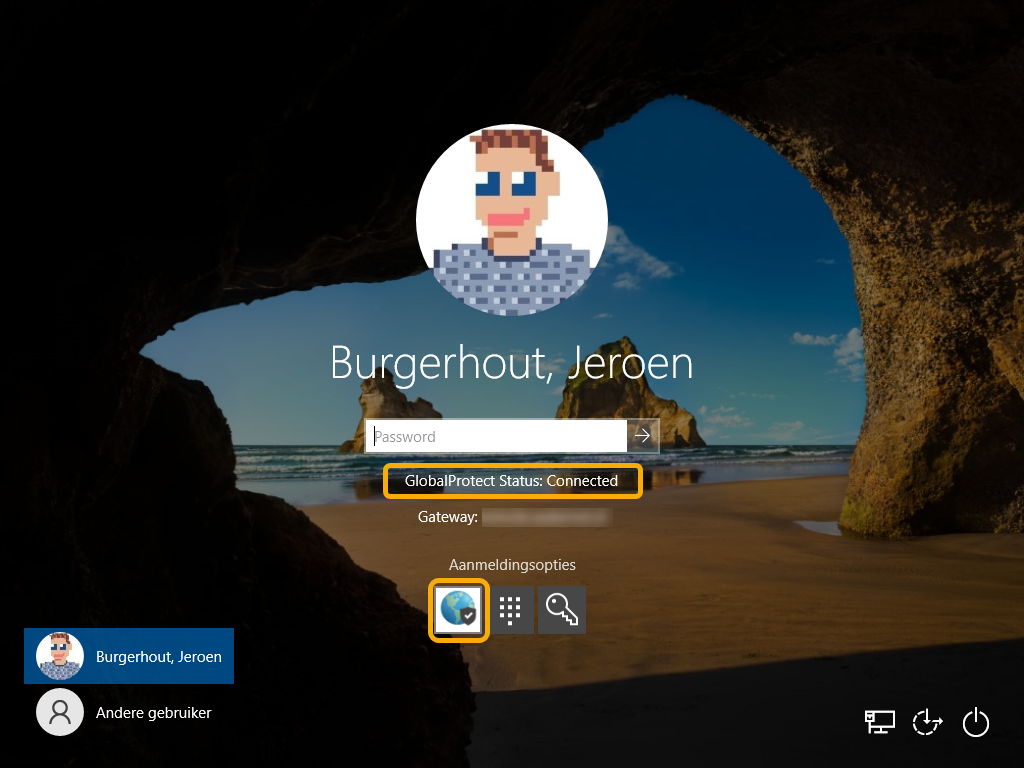
So far so good. However,...... after a reboot of a test machine, my password was no longer accepted. Uh? I didn't have a problem with that, did I? Not even while logging in after Autopilot's userphase? 🤔
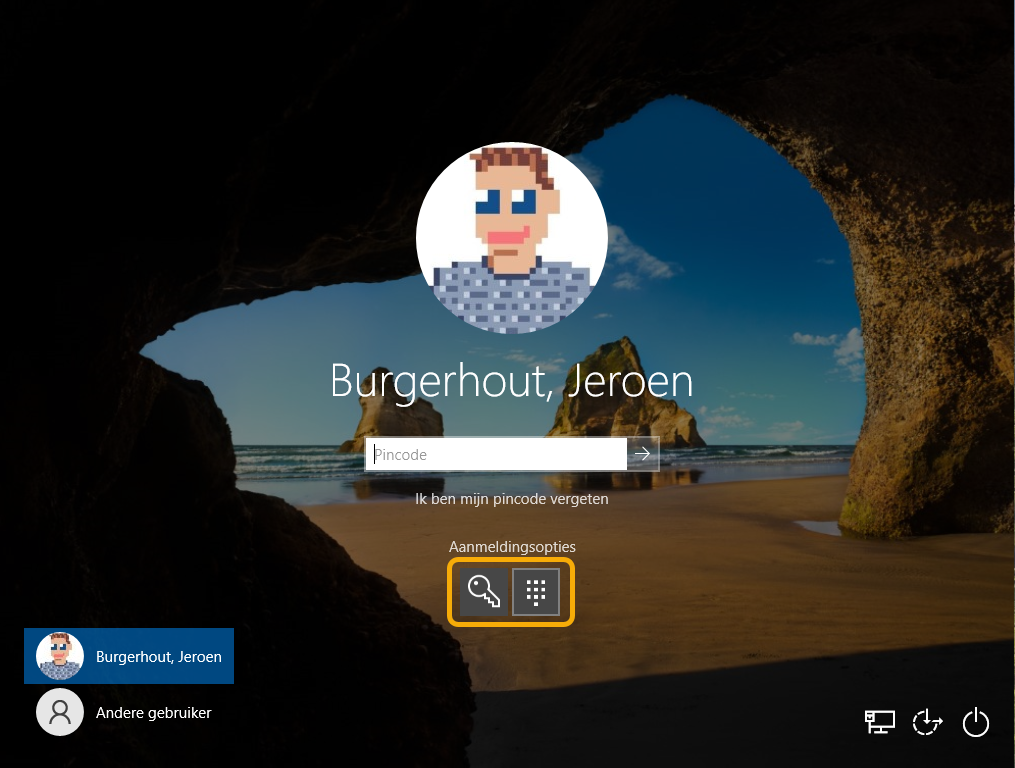
So I clicked on "login options" and saw the Global Protect icon as default. In other words, entering your WHfB PIN (numeric or alphanumeric) could only be done if you had clicked on the "PIN" icon. So this was annoying for the pilot users and myself, among others.
After some googling, I came across this blogpost from Peter van der Woude, with the explanation of how you can use the Exclude credential providers setting in the Settings Catalog in Intune. But first I had to uncover the credential GUID of the Global Protect VPN client. After some digging in the registry, I came across this GUID: {25CA8579-1BD8-469c-B9FC-6AC45A161C18}.
We can now use this GUID to hide the Global Protect icon on the sign-in screen and that this is no longer a default option to log in with.
Let's implement this and see what kind of result it gives.
Create the policy
- Go to the Enpoint Manager portal
- Go to Devices ➡️ Windows ➡️ Configuration Profiles and click on + Create profile
- In the dropdown list, select Windows 10 and later as platform and Settings Catalog as profile type
- Click on Create
- Give the policy a Name and click on Next
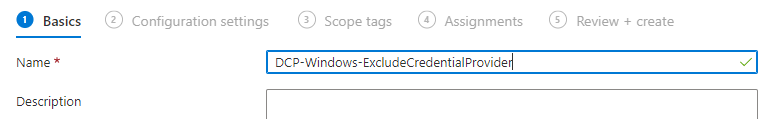
- Click on + Add settings
- Type in the search field exclude credential and hit Search
- Click on Administrative Templates\System\Logon and select Exclude credential providers
- Enable the setting
- Fill in the GUID
{25CA8579-1BD8-469c-B9FC-6AC45A161C18}
- Click on Next
- Click on Next
- Assign this policy to your desired AzureAD device group
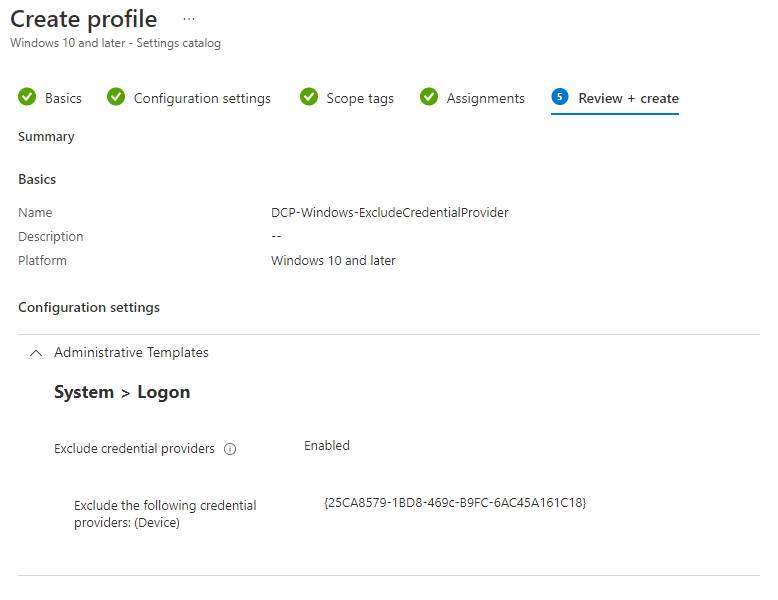
The end result
We have created a configuration profile, using the steps above. Now we have to wait for a device to pick up the new policy. 🕝
If all goes well, the Global Protect icon should have been removed and the WHfB PIN should be the default login method. The VPN client is then active in the background.
Thanks for reading this post. See you next time!